Hacking Your Pacemaker
The hack
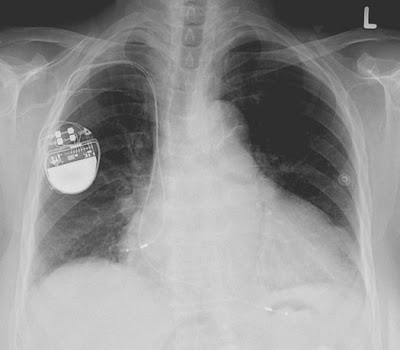
Pacemaker-hacking feels like a Hollywood plot. Assassinate someone by taking over the medical device that controls his heart? Surely that isn't possible in the real world.
Pacemaker-hacking feels like a Hollywood plot. Assassinate someone by taking over the medical device that controls his heart? Surely that isn't possible in the real world.
Actually, it's totally possible. Last year, a researcher demonstrateda pacemaker hack in Australia, with a virus that could conceivably spread from one person to every electronically assisted heart within 30 feet.
The threat level
Probably limited to assassination targets. Think: high-profile people, who have pacemakers. It would be an elaborate attack, though, since you need more than just an internet connection to pull it off. Odds are that anyone interested in doing this could get a bomb or a pistol to the target cheaper and faster. This is Hollywood not because it's impossible, but because it's not very efficient.
Probably limited to assassination targets. Think: high-profile people, who have pacemakers. It would be an elaborate attack, though, since you need more than just an internet connection to pull it off. Odds are that anyone interested in doing this could get a bomb or a pistol to the target cheaper and faster. This is Hollywood not because it's impossible, but because it's not very efficient.
Crashing A Plane
The hack
The prospect of a terrorist taking over an airplane is never a pleasant one, and given that today a plane can almost pilot itself, all that a potential hijacker has to do is get into the airplane's computers--he doesn't even need to be on the actual airplane.
The prospect of a terrorist taking over an airplane is never a pleasant one, and given that today a plane can almost pilot itself, all that a potential hijacker has to do is get into the airplane's computers--he doesn't even need to be on the actual airplane.
This is well within the realm of possibility; there's going to be a demonstration on how to remotely hack an airplane at an upcoming security conference. This is apparently a particular worry for higher-end corporate jets, which may be more vulnerable than traditional commercial jets because they offer easier external access to internal computer systems--great for fast communication, but also for hackers.
Surely air traffic control is safe? Afraid not. Past security conferences have demonstrated that the future air traffic control console can be overwhelmed by false signals.
The threat level
The technological vulnerabilities are certainly worrisome, but airplanes really haven't been a popular terrorism target since 2001. Just because something is a passe target doesn't mean we should forget about it. But it makes more sense to understand what kinds of attacks terrorists like to do, and protect against those, rather than ones they could conceivably do but haven't done. These days, the popular attacks mostly involve bombs on the ground.
The technological vulnerabilities are certainly worrisome, but airplanes really haven't been a popular terrorism target since 2001. Just because something is a passe target doesn't mean we should forget about it. But it makes more sense to understand what kinds of attacks terrorists like to do, and protect against those, rather than ones they could conceivably do but haven't done. These days, the popular attacks mostly involve bombs on the ground.
Breaking The Electrical Grid
The hack
Power outages kill more people than you'd think. Air-conditioning shuts off; stores, pharmacies, and hospitals close; cell phone service gets disrupted--all of which can be deadly, especially for vulnerable populations. According to a study on the human costof the 2003 power outage in New York, 90 deaths can be directly linked to the outage (that's 15 times more than New York's official total of 6). That blackout was caused by a small bug in a regional power company, but the consequences quickly spread and left up to 55 million people without power for three days.
Power outages kill more people than you'd think. Air-conditioning shuts off; stores, pharmacies, and hospitals close; cell phone service gets disrupted--all of which can be deadly, especially for vulnerable populations. According to a study on the human costof the 2003 power outage in New York, 90 deaths can be directly linked to the outage (that's 15 times more than New York's official total of 6). That blackout was caused by a small bug in a regional power company, but the consequences quickly spread and left up to 55 million people without power for three days.
What about a deliberate attack? Late last summer, hackers broke past a Canadian power company's security and gained access to the electrical controls. The hackers didn't wreak any havoc, but they could have. Internet-connected smart grids are especially vulnerable, because they are increasingly hooked up to the regular internet, giving outsiders easy access.
The threat level
The best a cyberattack could hope for is to hit a smaller power provider, mess with its controls, and have that spiral up into a much larger outage. But a small attack that mimics, say a power line failure, is what power companies spend time and money trying to prevent. And nowadays--especially since the 2003 outage--power companies have controls in place to avoid such mishaps. Chances are a small attack wouldn't provoke a bigger outage.
The best a cyberattack could hope for is to hit a smaller power provider, mess with its controls, and have that spiral up into a much larger outage. But a small attack that mimics, say a power line failure, is what power companies spend time and money trying to prevent. And nowadays--especially since the 2003 outage--power companies have controls in place to avoid such mishaps. Chances are a small attack wouldn't provoke a bigger outage.
Power outages are also an incredibly imprecise way to attack a target, and it's hard for a terrorist group to claim credit for something that could easily have been a simple sensor error.
While it's possible to gain access to the controls of a small part of the grid, it'd be extremely difficult, time-consuming, and expensive for hackers to mount a larger attack. Writing for Motherboard, Brian Merchant says "In this case, it would be a terrorist cell hellbent on using a massive amount of time and resources to … cause a temporary blackout??"
Unlikely.
Wrecking Your Car
The hack
The same remote-controlled security systems that protect cars from burglars may open them up to cyber attacks. In 2010, researchers in automotive electronic security demonstrated that aphysical device could be installed in a car to give remote access to a malicious third party. Since then, the ability to take over a car's controls from afar has only grown. A study published in 2011 by the same researchers demonstrated that there are multiple wireless ways to access a car remotely. Systems like OnStar, which can disable and drive a car if it's reported stolen, can be accessed through cellular networks.
The same remote-controlled security systems that protect cars from burglars may open them up to cyber attacks. In 2010, researchers in automotive electronic security demonstrated that aphysical device could be installed in a car to give remote access to a malicious third party. Since then, the ability to take over a car's controls from afar has only grown. A study published in 2011 by the same researchers demonstrated that there are multiple wireless ways to access a car remotely. Systems like OnStar, which can disable and drive a car if it's reported stolen, can be accessed through cellular networks.
What can attackers do once they've gained access to your car? They could take over brakes, lights, and engines. That's a problem.
The threat level
The trick, like most of these cyber attacks, is that it's an elaborate way for an assailant to do something that's much simpler with a handgun. The amount of information you have to gather beforehand--to find the car of the person you want to kill and the times that person will be in his or her car--make for a good Hollywood montage, but that's about it.
The trick, like most of these cyber attacks, is that it's an elaborate way for an assailant to do something that's much simpler with a handgun. The amount of information you have to gather beforehand--to find the car of the person you want to kill and the times that person will be in his or her car--make for a good Hollywood montage, but that's about it.
What if some sadistic person just wanted to start hacking cars and driving them into things? That's a pretty irrational use of the skill it would take to do this, but if someone were so inclined, he or she would certainly ruin the lives of those involved in the crashes. For everyone else, it'd just make for another moderately bad commute.
Crashing A Drone Into Your Skull
The hack
Drones, that ubiquitous specter of technological doom covering front pages everywhere, can indeed be hacked. Or at least spoofed, which is like hacking if all a hacker could do was give the drone new directions and sometimes make it crash. The most famous case of this is when Iran allegedly captured the United States's stealth drone RQ-170, but similar stuff has happened stateside, too. Last summer, on a dare from the Department of Homeland security, students at University of Texas Austinspoofed a government drone.
Drones, that ubiquitous specter of technological doom covering front pages everywhere, can indeed be hacked. Or at least spoofed, which is like hacking if all a hacker could do was give the drone new directions and sometimes make it crash. The most famous case of this is when Iran allegedly captured the United States's stealth drone RQ-170, but similar stuff has happened stateside, too. Last summer, on a dare from the Department of Homeland security, students at University of Texas Austinspoofed a government drone.
In 2015, the FAA will clear new airspace for drones, and we'll truly be living in the drone age. Of course, researchers, police departments, and universities are already cleared to fly drones inplenty of places in the United States, so the possibility of a rogue spoofed drone already exists. This is a big concern for Congress, which wants to make sure that drones are not an excessive risk to add to our skies. The image of dozens of robots falling from above is nothing a politician wants to explain in a reelection campaign.
The threat level
You can only spoof one drone at a time, and there is only so much harm you can cause by feeding an unarmed machine the wrong GPS information. Given the average size of drones, like the Parrot AR.Drone 2.0 pictured here, the death total would be limited to one or two people. The story of Aeschylus, an ancient Greek playwright who died when an eagle dropped a turtle on his bald head, suggests that death-by-flying object isn't impossible, but it is very unlikely.
You can only spoof one drone at a time, and there is only so much harm you can cause by feeding an unarmed machine the wrong GPS information. Given the average size of drones, like the Parrot AR.Drone 2.0 pictured here, the death total would be limited to one or two people. The story of Aeschylus, an ancient Greek playwright who died when an eagle dropped a turtle on his bald head, suggests that death-by-flying object isn't impossible, but it is very unlikely.




No comments:
Post a Comment